Boot Order
Boot Sequence
Power on : syscon boots from it's internal (non-encrypted / dual banked) ROM *1 *2
+ syscon powers up various power subsystems + syscon powers up cell and checks status + syscon sends Cell configuration ring to Cell + syscon pulls the reset of Cell high -> Cell INIT
Cell INIT: CELL boots from it's internal ROM *2
+ Initialises I/O + fetches encrypted bootldr off NAND/NOR flash (at address 0xF00000) + Initialises RAM + loads bootldr into Isolated SPU (SPE0) + Runtime Secure Boot decrypts and verifies bootldr and executes + bootldr decrypts lv0 which runs on PPU -> loaders INIT
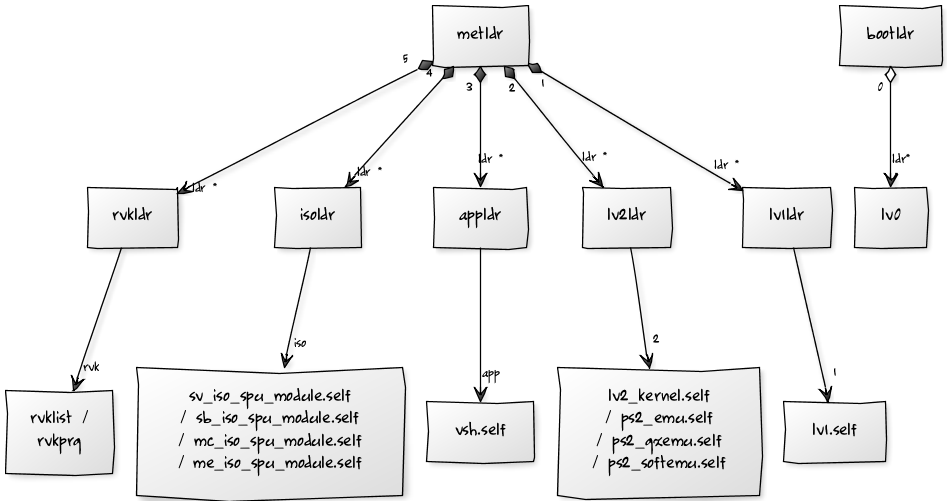
loaders INIT: lv0 loads metldr (SPE2)
+ passes lv1ldr (which loads lv1) to metldr + passes lv2ldr (which loads lv2) to metldr + passes appldr (which loads vsh) to metldr + passes isoldr (which loads *.iso_spu_module) to metldr + passes rvkldr (which loads rvkprg / rvklist) to metldr
- 1) Read/Writeable with undocumented / should also be read/writeable through serial port and possible to switch it to the backup bank1 with backup_mode pulled high
- 2) CEX/Retail consoles go to standby with red light. SEX/SHOP/SECH will not standby, but instead boot through without waiting for powerbutton. Also check is done on all models if update is flagged to set it into firmware updating procedure
- 3) Partialy Read/Writeable
about the disabled SPE: syscon reads it’s internal (non-encrypted) eeprom @ 0x48C30 which is value 0×06 on all CEX/Retail consoles and will set the cell config ring accordingly for 7 SPE’s. SPE0 and SPE2 are reserved for bootldr and metldr for isolation respectively. Setting the value to a nonworking state (e.g. 0×00, 0xFF, enabling a defective SPE or disabling a needed SPE for proper boot) might brick the console, locking you out from restoring the correct value to the syscon eeprom.
Chain of Trust
| Name | Location | Processor | Encryption | Updateable | Revokable | Usage | Exploited |
|---|---|---|---|---|---|---|---|
| Runtime Secure Boot | Hardware based | Cell | Hardware Based | no | no | Verification of images loaded into isolated SPE | no |
| bootldr (Boot Loader) | NAND/NOR (0xFC0000) | SPE(0) | Per Console Encrypted at factory | No | No | Boot lv0 | No |
| lv0 (Level 0) | NAND/NOR (COREOS) | PPU | Static Encryption / Signed | Yes | No | Setup Hardware | No |
| metldr (Meta Loader) | NAND/NOR (asecure_loader) | SPE(2) | Per Console Encrypted at factory | No | No | Run loaders | Yes |
| lv1ldr (Level 1 (Hypervisor) Loader) | NAND/NOR (COREOS) | SPE(2) | Static Encryption / Signed | Yes | No | Decrypt lv1 (Hypervisor) | Yes |
| lv2ldr (Level 2 (GameOS) Loader) | NAND/NOR (COREOS) | SPE(2) | Static Encryption / Signed | Yes | No | Decrypt lv2 (GameOS) | Yes |
| appldr (Application Loader) | NAND/NOR (COREOS) | SPE(2) | Static Encryption / Signed | Yes | Yes | Decrypt games | Yes |
| isoldr (Isolation Loader) | NAND/NOR (COREOS) | SPE(2) | Static Encryption / Signed | Yes | No | Decrypt modules | Yes |
| rvkldr (Revokation Loader) (Discarded after 0.8) | NAND/NOR (COREOS) | SPE(2) | Static Encryption / Signed | Yes | No | decrypt revoke list | Yes |
Chain of trust Diagram
Cell BE Configuration Ring
This data was captured from the SPI bus connecting CELL to SYSCON and parsed as per the Cell BE 90nm HIG. See the full SPI dump for more boot-time communication over SPI.
| Offset | Length | PS3 Value | Description |
|---|---|---|---|
| Pervasive Logic (PRV) Bits | |||
| 0000 | 002 | 0b00 | reserved |
| SPE_1 Bits | |||
| 0002 | 009 | 0b000000000 | reserved |
| 0011 | 015 | 0b000000000000000 | SPE1 MC_BASE |
| 0026 | 015 | 0b100000000000000 | SPE1 MC_COMP_EN |
| 0041 | 010 | 0b1110000000 | SPE1 IOIF1_COMP_EN |
| 0051 | 032 | 0x80000000 | reserved |
| 0083 | 040 | 0x2401fc00000 | SPE1 SReset??? |
| 0123 | 064 | 0x0000000000000802 | reserved |
| 0187 | 019 | 0b1000000000000000000 | SPE1 BE_MMIO_Base |
| 0206 | 004 | 0x0 | SPE1 unit Cell BE node ID |
| 0210 | 003 | 0b001 | SPE1 SPE ID |
| 0213 | 011 | 0b00110110000 | reserved |
| SPE_3 Bits | |||
| 0224 | 009 | 0b000000000 | reserved |
| 0233 | 015 | 0b000000000000000 | SPE3 MC_BASE |
| 0248 | 015 | 0b100000000000000 | SPE3 MC_COMP_EN |
| 0263 | 010 | 0b1110000000 | SPE3 IOIF1_COMP_EN |
| 0273 | 032 | 0x80000000 | reserved |
| 0305 | 040 | 0x2401fc00000 | SPE3 SReset??? |
| 0345 | 064 | 0x0000000000000802 | reserved |
| 0409 | 019 | 0b1000000000000000000 | SPE3 BE_MMIO_Base |
| 0428 | 004 | 0x0 | SPE3 unit Cell BE node ID |
| 0432 | 003 | 0b011 | SPE3 SPE ID |
| 0435 | 011 | 0b00110110000 | reserved |
| SPE_5 Bits | |||
| 0446 | 009 | 0b000000000 | reserved |
| 0455 | 015 | 0b000000000000000 | SPE5 MC_BASE |
| 0470 | 015 | 0b100000000000000 | SPE5 MC_COMP_EN |
| 0485 | 010 | 0b1110000000 | SPE5 IOIF1_COMP_EN |
| 0495 | 032 | 0x80000000 | reserved |
| 0527 | 040 | 0x2401fc00000 | SPE5 SReset??? |
| 0567 | 064 | 0x0000000000000802 | reserved |
| 0631 | 019 | 0b1000000000000000000 | SPE5 BE_MMIO_Base |
| 0650 | 004 | 0x0 | SPE5 unit Cell BE node ID |
| 0654 | 003 | 0b101 | SPE5 SPE ID |
| 0657 | 011 | 0b00110110000 | reserved |
| SPE_7 Bits | |||
| 0668 | 009 | 0b000000000 | reserved |
| 0677 | 015 | 0b000000000000000 | SPE7 MC_BASE |
| 0692 | 015 | 0b100000000000000 | SPE7 MC_COMP_EN |
| 0707 | 010 | 0b1110000000 | SPE7 IOIF1_COMP_EN |
| 0717 | 032 | 0x80000000 | reserved |
| 0749 | 040 | 0x2401fc00000 | SPE7 SReset??? |
| 0789 | 064 | 0x0000000000000802 | reserved |
| 0853 | 019 | 0b1000000000000000000 | SPE7 BE_MMIO_Base |
| 0872 | 004 | 0x0 | SPE7 unit Cell BE node ID |
| 0876 | 003 | 0b111 | SPE7 SPE ID |
| 0879 | 011 | 0b00110110000 | reserved |
| Cell Broadband Engine Interface (BEI) Unit Bits | |||
| 0890 | 002 | 0b00 | reserved |
| 0892 | 004 | 0x0 | BIF unit Cell BE node ID |
| 0896 | 022 | 0b1000000000000000000101 | BEI BE_MMIO_Base |
| 0918 | 003 | 0b110 | reserved |
| 0921 | 003 | 0b011 | reserved |
| 0924 | 012 | 0xf80 | IOIF1 base address mask |
| 0936 | 022 | 0b1001000000000000000000 | IOIF1 base address and replacement |
| 0958 | 012 | 0xf80 | IOIF0 base address mask |
| 0970 | 022 | 0b1010000000000000000000 | IOIF0 base address and replacement |
| 0992 | 002 | 0b00 | reserved |
| 0994 | 002 | 0b10 | AC0 configuration |
| 0996 | 005 | 0b00100 | BIF/IOIF0 receive (RX) configuration |
| 1001 | 006 | 0b000100 | BIF/IOIF0 transmit (TX) configuration |
| 1007 | 006 | 0b000000 | reserved |
| 1013 | 001 | 0b1 | BIF/IOIF0 coherency mode |
| 1014 | 003 | 0b000 | reserved |
| 1017 | 003 | 0b100 | BIF/IOIF0 I/O reorder mode for transmit |
| 1020 | 016 | 0x0000 | reserved |
| 1036 | 003 | 0b100 | IOIF1 I/O reorder mode for transmit |
| 1039 | 001 | 0b1 | reserved |
| 1040 | 002 | 0b10 | IOIF1 RX configuration |
| 1042 | 002 | 0b10 | IOIF1 TX configuration |
| 1044 | 032 | 0x00000200 | FlexIO PLL configuration |
| 1076 | 002 | 0b00 | reserved |
| EIB Unit Bits | |||
| 1078 | 002 | 0b00 | reserved |
| 1080 | 001 | 0b0 | AC0 livelock response control |
| 1081 | 004 | 0x0 | EIB unit Cell BE node ID |
| 1085 | 001 | 0b0 | AC1 configuration |
| 1086 | 001 | 0b1 | AC0 configuration |
| 1087 | 004 | 0x2 | AC0 command credits |
| 1091 | 022 | 0b1000000000000000000000 | LBAR0_cfg |
| 1113 | 022 | 0b1111111111111111111000 | LBAMR0_cfg |
| 1135 | 003 | 0b011 | reserved |
| 1138 | 001 | 0b0 | AC1 livelock response control |
| 1139 | 002 | 0b00 | reserved |
| SPE_6 Bits | |||
| 1141 | 009 | 0b000000000 | reserved |
| 1150 | 015 | 0b000000000000000 | SPE6 MC_BASE |
| 1165 | 015 | 0b100000000000000 | SPE6 MC_COMP_EN |
| 1180 | 010 | 0b1110000000 | SPE6 IOIF1_COMP_EN |
| 1190 | 032 | 0x80000000 | reserved |
| 1222 | 040 | 0x2401fc00000 | SPE6 SReset??? |
| 1262 | 064 | 0x0000000000000802 | reserved |
| 1326 | 019 | 0b1000000000000000000 | SPE6 BE_MMIO_Base |
| 1345 | 004 | 0x0 | SPE6 unit Cell BE node ID |
| 1349 | 003 | 0b110 | SPE6 SPE ID |
| 1352 | 011 | 0b00110110000 | reserved |
| SPE_4 Bits | |||
| 1363 | 009 | 0b000000000 | reserved |
| 1372 | 015 | 0b000000000000000 | SPE4 MC_BASE |
| 1387 | 015 | 0b100000000000000 | SPE4 MC_COMP_EN |
| 1402 | 010 | 0b1110000000 | SPE4 IOIF1_COMP_EN |
| 1412 | 032 | 0x80000000 | reserved |
| 1444 | 040 | 0x2401fc00000 | SPE4 SReset??? |
| 1484 | 064 | 0x0000000000000802 | reserved |
| 1548 | 019 | 0b1000000000000000000 | SPE4 BE_MMIO_Base |
| 1567 | 004 | 0x0 | SPE4 unit Cell BE node ID |
| 1571 | 003 | 0b100 | SPE4 SPE ID |
| 1574 | 011 | 0b00110110000 | reserved |
| SPE_2 Bits | |||
| 1585 | 009 | 0b000000000 | reserved |
| 1594 | 015 | 0b000000000000000 | SPE2 MC_BASE |
| 1609 | 015 | 0b100000000000000 | SPE2 MC_COMP_EN |
| 1624 | 010 | 0b1110000000 | SPE2 IOIF1_COMP_EN |
| 1634 | 032 | 0x80000000 | reserved |
| 1666 | 040 | 0x2401fc00000 | SPE2 SReset??? |
| 1706 | 064 | 0x0000000000000802 | reserved |
| 1770 | 019 | 0b1000000000000000000 | SPE2 BE_MMIO_Base |
| 1789 | 004 | 0x0 | SPE2 unit Cell BE node ID |
| 1793 | 003 | 0b010 | SPE2 SPE ID |
| 1796 | 011 | 0b00110110000 | reserved |
| SPE_0 Bits | |||
| 1807 | 009 | 0b000000000 | reserved |
| 1816 | 015 | 0b000000000000000 | SPE0 MC_BASE |
| 1831 | 015 | 0b100000000000000 | SPE0 MC_COMP_EN |
| 1846 | 010 | 0b1110000000 | SPE0 IOIF1_COMP_EN |
| 1856 | 032 | 0x80000000 | reserved |
| 1888 | 040 | 0x2401fc00000 | SPE0 SReset??? |
| 1928 | 064 | 0x0000000000000802 | reserved |
| 1992 | 019 | 0b1000000000000000000 | SPE0 BE_MMIO_Base |
| 2011 | 004 | 0x0 | SPE0 unit Cell BE node ID |
| 2015 | 003 | 0b000 | SPE0 SPE ID |
| 2018 | 011 | 0b00110110000 | reserved |
| MIC Bus Logic Bits | |||
| 2029 | 004 | 0x8 | reserved |
| 2033 | 016 | 0x0000 | MIC address space start |
| 2049 | 016 | 0xfffc | MIC address space end |
| 2065 | 030 | 0b100000000000000000010100001001 | PRV BE_MMIO_Base |
| 2095 | 030 | 0b100000000000000000010100001010 | MIC BE_MMIO_Base |
| 2125 | 004 | 0x3 | reserved |
| 2129 | 004 | 0x0 | MIC unit Cell BE node ID |
| 2133 | 002 | 0b00 | reserved |
| PowerPC Processor Unit Bits | |||
| 2135 | 009 | 0b000000000 | reserved |
| 2144 | 008 | 0x00 | PIR_defn |
| 2152 | 013 | 0b0000000000000 | reserved |
| 2165 | 040 | 0x2401fc00000 | PPE SReset Vector |
| 2205 | 224 | 0x000000000000000000000000008000000000000000000000000003c0 | reserved |
| PowerPC Processor Storage Subsystem (PPSS) Bits | |||
| 2429 | 061 | 0x008000000000400, 0b0 | reserved |
| 2490 | 001 | 0b1 | L2 livelock |
| 2491 | 044 | 0x000000f8000 | reserved |
| 2535 | 004 | 0x0 | PPE unit Cell BE node ID |
| 2539 | 009 | 0b011011000 | reserved |
| 2548 | 030 | 0b100000000000000000010100000000 | PPE BE_MMIO_Base |
| 2578 | 007 | 0b1000111 | reserved |
| 2585 | 001 | 0b1 | NCU 2 token decode |
| 2586 | 016 | 0x0000 | reserved |
| 2602 | 001 | 0b1 | NCU livelock |
| 2603 | 001 | 0b1 | PPE livelock |
| 2604 | 002 | 0b00 | reserved |
| MIC Bits | |||
| 2606 | 016 | 0x0000 | XIO PLL LO |
| 2622 | 016 | 0x9cfc | XIO PLL HI |
| 2638 | 004 | 0x0 | reserved |
| PRV Bits | |||
| 2642 | 006 | 0b011111 | Thermal overload temperature |
| 2648 | 027 | 0b000001010001000000000011000 | reserved |
| 2675 | 001 | 0b1 | Pervasive logic livelock |
| 2676 | 010 | 0b0000000000 | reserved |
| 2686 | 008 | 0x08 | SPE disable |
| 2694 | 003 | 0b011 | reserved |
Runtime Secure
This runtime secure boot, in fact, is tightly coupled with an SPE entering isolation mode. An application must go through the hardware authentication step before it can execute on an isolated SPE. When isolation mode is requested, first, the previous thread is stopped and cancelled. Then, the hardware will automatically start fetching the application into the LS, and the hardware will verify the integrity of the application. If the integrity check fails, the application will not be executed. The check can fail for one of two reasons. The application might have been modified within memory or storage. Then, the assumption is that the functionality might have changed and it cannot be trusted anymore. Or, the writer of the application does not know the cryptographic secret that is needed for a successful authentication. Otherwise, if the authentication check is successful, the hardware will automatically kick-start the application's execution in isolation mode. Because the hardware controls all of these steps, the verification of the application's integrity cannot be skipped or manipulated and will happen consistently and correctly.
http://www.ibm.com/developerworks/power/library/pa-cellsecurity/
Changes in firmware 3.60
Lv0 has now been changed, LV0 now appears to encapsulate all of the loaders (lv1ldr, lv2ldr, appldr, isoldr). Now in order to break the chain of trust we need to be able to decrypt/exploit LV0 which at this time has not been done.