Talk:Validating flash dumps
Basic steps to verify if your bios dump is correct:
What you need:
Your ps3 Bios Backup, extracted via e3 flasher (bkps3.bin)
e3 nor dump checker v1.0 (should be used only as a complement, as it gives false positives)
Flowrebuilder v4.2.2.0
HxD - Hex Editor
Now if you follow this basic steps, and if everything matches your ps3dump is OK, if anything fails to match use another dump, the one you're checking may lead you to a permanent brick
0 - open e3 nor dump checker, and check if it gives any errors.
WARNING: Don't trust only in dump checker, as it's known for it's false positives.
Statistics analysis
1.1 - Open your bkps3.bin in HxD
1.2 - select analysis > statistics > select your file
1.3 - mouse over the blue bars and check if between known good range:
Valid dumps will have
| Value | NAND | NOR |
|---|---|---|
| 00's | 1.43% - 2.68% >3838627 <7194070 |
18.38% - 29.01% >3083652 <4867070 |
| FF's | 18.25% - 24.54% >48989471 <65874061 |
10.42% - 10.48% >1748186 <1758252 |
| rest | below 0.5% <1342177 |
below 0.5% <83886 |
Note: if you get deviating statistics (since 3.60 CoreOS/ROS will deviate because of lv0 loaders encapsulation, 00's NOR statistics thus will be above/equal 18.23% and below 18.38%). Prepatch it so that both ROS and RVK areas are filled with 3.55 reference data. If still bad statistics, it means dump is bad in perconsole regions, prone to permabrick!
Make Visual inspection
Extracting
- Open Flowrebuilder
- select "byte reverse and EXTRACT a NOR dump File"
- select the desired bkps3.bin , and then execute operation
- the Dump extraction should've been done without any errors, otherwise it may lead you to a permanent brick.
- after extracting you should have the following output: bkps3.swap.bin and bkps3.swap.ext
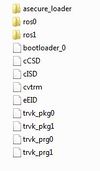
- inside the folder bkps3.swap.ext you should have the following items:
asecure_loader (folder)
ros0 (folder)
ros1 (folder)
bootloader_0 (.bin)
cCSD (.bin)
cISD (.bin)
cvtrm (.bin)
eEID (.bin)
trvk_pkg0 (.bin)
trvk_pkg1 (.bin)
trvk_prg0 (.bin)
trvk_prg1 (.bin)
(if you don't have them, please don't proceed! try to extract the dump again, or use an diferent dump, the one you're using will probably lead you to a permanent brick)
Checking seperate files/sections
Metldr
http://www.ps3devwiki.com/wiki/Flash:asecure_loader
open the file \asecure_loader\metdlr in HxD, then ctrl + a
look for your values in the following table:
http://www.ps3devwiki.com/wiki/Validating_flash_dumps#Check_metldr.2Bbootldr_sizes ,
and check if your lenght field in HxD matches with Size field in the table.
Also check the binary is complete, without FFFF or 0000 repetition (there should only be 0000 in header @ 0x0 of binary)
Bootldr
http://www.ps3devwiki.com/wiki/Flash:bootldr
repeat the process with Bootloader_0.bin File
make sure your bootloader_0(bin) file starts proper: look at offsets 2 and 12 and compare the values against Validating_flash_dumps#Check_metldr.2Bbootldr_sizes
Also check the binary is complete, without FFFF or 0000 repetition (there should only be 0000 in header @ 0x0 of binary)
Header
http://www.ps3devwiki.com/wiki/Flash:0FACE0FF_DEADBEEF
http://www.ps3devwiki.com/wiki/Flash:Flash_Format
open your bkps3.swap.bin with HxD and check if the both sections matches.
Table
http://www.ps3devwiki.com/wiki/Flash:Flashregion_Table
From offset 00000400 to 00000600 (search for offset in HxD do ctrl + g) you should have the following:
http://www.ps3devwiki.com/images/3/3e/HxD.png
Flashregion Table
http://www.ps3devwiki.com/wiki/Flash:Flashregion_Table + http://www.ps3devwiki.com/wiki/Flash:asecure_loader
Search now for the following Hex code: 617365637572655F6C6F616465720000 for it in Hxd, do ctrl+f change the datatype field for HEX, Copy and paste the code, it should be found and looks like sample.
eEID
http://www.ps3devwiki.com/wiki/Flash:Encrypted_Individual_Data_-_eEID
cISD
http://www.ps3devwiki.com/wiki/Flash:Individual_System_Data_-_cISD
search for your Serial
it should be in offset 003F090, you can also look for the 2nd part of your serial number (ex: xx-12345678-xxxxxx)
cCSD
http://www.ps3devwiki.com/wiki/Flash:Common_System_Data_-_cCSD
CVTRM
http://www.ps3devwiki.com/wiki/Flash:cvtrm (cvtrm))
ROS
http://www.ps3devwiki.com/wiki/Flash:ROS#ros0
http://www.ps3devwiki.com/wiki/Flash:ROS#ros1
RVK
http://www.ps3devwiki.com/wiki/Flash:Revoke_Program
http://www.ps3devwiki.com/wiki/Flash:Revoke_Package
Second Region
http://www.ps3devwiki.com/wiki/Flash:0FACE0FF_DEADFACE
CELL_EXTNOR_AREA
http://www.ps3devwiki.com/wiki/Flash:CELL_EXTNOR_AREA
search for your HDD brand ( ctrl+f and in text mode type the disk brand) or else ctrl + g and it sould be on the 00F20200 offset
these are the basic steps to check your dump file, however if you wish to go further and check your dump more in dept, please check:
After Checking all those fields, if everything checks, so your dump is OK and you're good to proceed with your flashing process. always make more than 1 backup of your bios.
all the credits for this tutorial goes to the @p users of irc channel #ps3downgrade at Ef.net especially to alex07 and eussNL who taught me and helped me with the basic how-to for cheking the dumps. all i just did was to compile all the info they gave me and wrote everything down for further use. after writing everything done i thought it could be useful for everyone.
hope it helps.
Feel free to correct any bad english or any mistaken info in this how to.
best regards cfcolaco
Other dumpcheckers
https://github.com/Swizzy/PS3DumpChecker/
Would you like me to update my BwE NOR Validator for 2018?
Please provide me with the relevant MD5's within ros0/1 etc and I will be happy to do this.
Easy way to do this would be to use the validator on valid flashes starting from firmwares that aren't included in my original validator and then provide me with the apparent 'DANGER' outputs. I can then quickly add them to the updated validator as valid results.
It would take me far too long to do this myself and I am busy with the PS4 NOR Validator.
Here is what is in the latest BwE NOR Validator, as you can see beyond 4.31 is not included:
4.31 5888F186C7B1B5198F221806201CE7AC 4.30 C7398C79576A90888DE0887DB9B5FA46 4.25_DEX 274BB74ABFB47DE9E9E05BBA154E4D5D 4.25 FFC76060A2A48FBE91E577064A343878 4.23 5F47FDEFAD2949D534A55A6D9BB5661B 4.21 9A01E6AC0F70D4AE33ACAE0C6B17C66B 4.20 6ABEC8C997E6CBDB6B07A31CEBB15128 4.11 F57AF374CC32D73068C98BD9FF0886D9 4.10 87C511E4FC9E51FE6B424A09A409DFEC 4.00 7772192FC02919457D97537DD41900B8 3.73 A0827D76F362D303A25A3103156F5B70 3.72 9E8D2C63D432B1A1E53FD05AB8E5262A 3.70 010CF52C1947997D2C44473726116305 3.66_DEX B5ADBFD3D80F059BD4B83A0CC300F568 3.66 974CDEA2E646758EF40D659957F6E93B 3.65 8005B653D1A28FC9592145DC33DFA64F 3.61 4DA682B0A4408475D789B9C49AFEE737 3.60_DEX C80CCC2D6CCEE7A200E5E3C6A4DA9A7E 3.60 FA0AC8FFDCC06A8C39179017F150BA88 3.56_2 128CC2CDC5986C3C9F4DD56E74DEF184 3.56_1 4474E75E93D66E15377339F96A5D13F2 3.56_PATCHED 6CE56CC2BD4238E831E9A64E4547A81B 3.55_PATCH FCEAC0A025F8225E523FA190B38B540C 3.55_PATCHED F162E0D72EBA0F46B7FB36E6AAB63958 3.55_DEX 102E229DF047C1693ABFBFF5707BE84C 3.55 A974F88457424AC6D8E262DBF3ED7AA0 3.50_DEX 38BBDF08BA848FD1AD170B37A7BFD143 3.50 54AA1F0FF3F10F9806544C8E38E5ED3F 3.42 4E9BDDA7EF6E34B1FA433DD016F6CA2A 3.41_DEX AFE1199881B1C015DF29092C49EFEEFA 3.41_2 C2FE27A86B3174685B5BB15917F27381 3.40 99A69A693A3E268D188623DE4C937CFC 3.30 2DA64B79AC538E7AF643A7E0F0FA64D0 3.21 2DC52F5E40F1B9560C760752477599AB 3.15_DEX D1E4A20987FE6FDD0BA446197005CBD7 3.15 38B9881CD317734B345E10C1FBBD8D45 3.10 46B80BF64C20157AD4B0CD6FFB536CB2 3.01 47D078F5F298743B435002A7C0FEED8A 3.00 B988CB3582838CC18F8B7D150074248E 2.80 BE82801857BADA8FFA9A353F10E23CDB 2.76 1F53B042118AE44B9C7939D887882785 2.70 094A2E6772B8548019BFADA384828E5A 2.60 93DDE807275889858514B72C8C52E3FD 2.53 968B4AB41D973D83BB34F4586EAAA3EE 2.52 85ED932A7ED992A8609B691EB20C8A4A 2.50 0F214D76731708447829ACCC5756D4A6 2.43_LEAKED_JIG 4C503EC4737A08F79FD8B4A4DFE0F31F 2.43 0647A46118311E2D20E7D09205B9D5EB 2.42 DB010865DB5E2D73782173D992C9B3EB 2.41 41852D3A1EB5DD8DF253926A61162AF5 2.40 08F7264FF08018BA346EBFCC96A2398D 2.36 773E896E3F0ED2E8FA30E000BC39A2DC 2.35 8E90D6483CCB71AA78780AAF43CC42F8 2.30 580E9F9C41CB2D4FE02687FD043C0B0E 2.20 249C426A359C30C93ECBB65B58C27FBA 2.17 FD2166CB121C8A4382B9872C5F06BB8B 2.10 9E03564621E6428276FD8D48AC2D15E9 2.01 FC81DF6DEAF57F8866C1B317821C0BD6 2.00 A0E7CE5FB1EF51BED74C0F0A0F682EA8 1.93 6162C9872A5126876054F306968F8451 1.92 FF600639D3A4D33B5040D14C3AABFD08 1.90 6CD39C1EB20D8B490931C19932F43966 1.82 33244E28A563D43B841DCCDA3D60B13F 1.81 88D2FAF7EDE04E5BA0CAEF8635BDEF58 1.80 4FE54D3DC7F455A4E8644831C36D6FF1 1.70 F08F35028CB26728BFCE879AF8360549 1.60 9195FDDBA5EB8E5497EBF66BB21E92FD 1.54 15DF1230C9B399D8BD09194B2C6B02E9 1.51 3022F1A15DA9669DA2FAC7B9727B2694 1.50 5CD5B52F46B156A73EA2BEE9235D99D1 1.32 41CEF7D4DAEEDEE28BDED8EC9D045098 1.31 763A0DE3F5AB7E63DFD899691E234621 1.30 EED51CF6C6E86496FA779C100BA11BA4 1.11 ED918905097A954C3827B991B1CC527E 1.10 371375E22B6EB5DFC75BE864D4493978 1.02 77DB1082B0C808D28A36C96A7468F5E5