Communication Processor
| This article is marked for rewrite/restructuring in proper wiki format. You can help PS3 Developer wiki by editing it. |
Hardware
CXD9790GG (I/O)
TCP-510 (Board ID on the DEH models such as DEH-R1040)
TCP-520 (Board ID on the DECR-1000)
(TCP-510 matches the TMU-510 motherbord, while TCP-520 matches the TMU-520 motherboard) The PSP DTP-T1000 unit also sports a communication processor but it does not come as a separate board, the hardware is integrated/soldered directly to the motherboard, unlike the PS3 CP, it does not run the firmware from RAM (the PS3 CP copies the firmware from ROM to RAM at boot so changes are, by default not persistant) and therefore writes files directly to flash.
CEB units feature a PCI slot capable of harboring a CP daughterboard (Sony used such setups as System Debuggers before DEH units came along), CP boards switched to a proprietary interface and shipped to 3rd parties starting with DEH-Rx
Software
De/Encrypt Communication Processor updates
This is how to decrypt/encrypt Playstation 3 Reference Tool Communication Processor updates. (use this knowledge wisely)
This was achieved by exploiting the communication processor firmware and gaining root privileges on the running Montavista Linux. The key for the CP update packages is located within the toolupdatedec binary located at /usr/local/sony/bin/toolupdatedec
The update packages are just tar.gz packages encrypted using AES256CBC Here is the syntax to decrypt them :
- The first 16 bytes of the package is the IV, the Second 16 bytes is the hash of the decrypted package.
So use this Syntax after skipping the first 32 bytes of the file:
openssl aes-256-cbc -in reftool_cp_xxx.bin -K E8ED2B817207B70C5DF9090507AF2A8982967620D692B92A59231638402DF13F -iv the_first_16_bytes_of_the_file -d > dec.tgz
PSP Hardware Tool Updates use the very same encryption but a different key inside the toolupdatedec binary.
The key to these units has also been dumped, here is the syntax to decrypt psp Hardware Tool Update for DTP-T1000
openssl aes-256-cbc -in psptoolupdate.bin -K A400C48628A7A5294D11AE3BB2587AEA32E501C63E49D1DCAA19B5AEB092F3DB -iv the_first_16_bytes_of_the_file -d > dec.tgz
P.S. If you have any trouble extracting the tarballs, try using Linux.
- Mathieulh
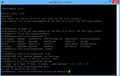
Because a picture is worth a thousand words, here is one:
Proper De/Encrypting of CP Updates
- source code cp-update-crypt Gitorious
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||